Microsoft Launches Windows Resiliency Initiative to Boost Security and System Integrity
Microsoft has announced a new Windows Resiliency Initiative as a way to…
NHIs Are the Future of Cybersecurity: Meet NHIDR
The frequency and sophistication of modern cyberattacks are surging, making it increasingly…
Hackers Exploiting NFCGate to Steal Funds via Mobile Payments
Threat actors are increasingly banking on a new technique that leverages near-field…
Decades-Old Security Vulnerabilities Found in Ubuntu’s Needrestart Package
Multiple decade-old security vulnerabilities have been disclosed in the needrestart package installed…
Why Privileged Access Security Must Be a Top Priority
Privileged accounts are well-known gateways for potential security threats. However, many organizations…
Hackers Hijack Unsecured Jupyter Notebooks to Stream Illegal Sports Broadcasts
Malicious actors are exploiting misconfigured JupyterLab and Jupyter Notebooks to conduct stream…
Ngioweb Botnet Fuels NSOCKS Residential Proxy Network Exploiting IoT Devices
The malware known as Ngioweb has been used to fuel a notorious…
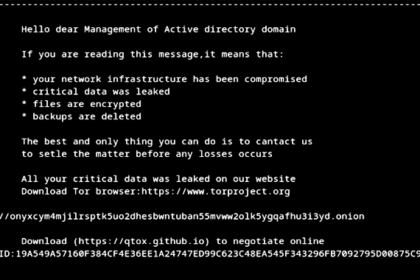
New ‘Helldown’ Ransomware Variant Expands Attacks to VMware and Linux Systems
Cybersecurity researchers have shed light on a Linux variant of a relatively…
THN Recap: Top Cybersecurity Threats, Tools, and Practices (Nov 11
What do hijacked websites, fake job offers, and sneaky ransomware have in…