Acronym Overdose – Navigating the Complex Data Security Landscape
In the modern enterprise, data security is often discussed using a complex…
12 Min Read
Fake Google Meet Pages Deliver Infostealers in Ongoing ClickFix Campaign
Threat actors are leveraging fake Google Meet web pages as part of…
3 Min Read
U.S. and Allies Warn of Iranian Cyberattacks on Critical Infrastructure in Year-Long Campaign
Cybersecurity and intelligence agencies from Australia, Canada, and the U.S. have warned…
4 Min Read
North Korean IT Workers in Western Firms Now Demanding Ransom for Stolen Data
North Korean information technology (IT) workers who obtain employment under false identities…
5 Min Read
Webinar on Building a Strong Data Security Posture
Picture your company's data as a vast, complex jigsaw puzzle—scattered across clouds,…
2 Min Read
SideWinder APT Strikes Middle East and Africa With Stealthy Multi-Stage Attack
An advanced persistent threat (APT) actor with suspected ties to India has…
6 Min Read
Researchers Uncover Cicada3301 Ransomware Operations and Its Affiliate Program
Cybersecurity researchers have gleaned additional insights into a nascent ransomware-as-a-service (RaaS) called…
4 Min Read
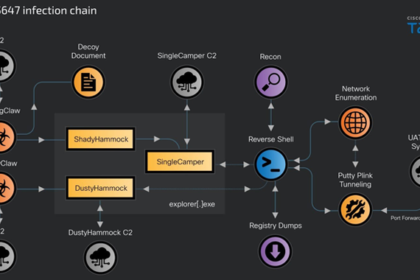
Russian RomCom Attacks Target Ukrainian Government with New SingleCamper RAT Variant
The Russian threat actor known as RomCom has been linked to a…
3 Min Read
5 Ways to Reduce SaaS Security Risks
As technology adoption has shifted to be employee-led, just in time, and…
7 Min Read